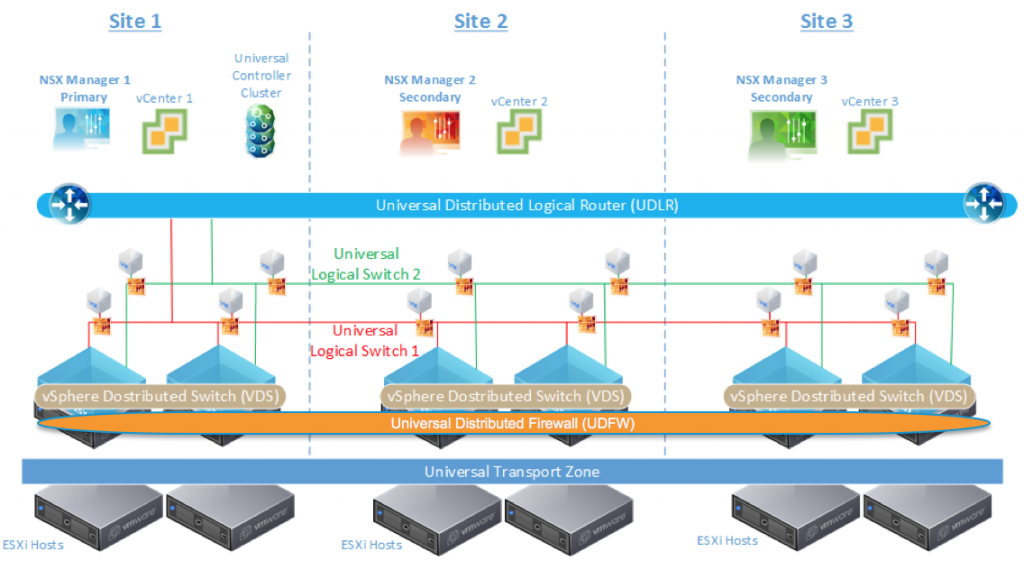
Recently I have had a task to reorganize NSX Cross vCenter domains - Primary and Secondary environments. My customer had eight vCenter with NSX - four pairs of Primary and Secondary. As you probably know or you can check on VMware page, benefits of Cross-vCenter NSX:
- Increased span of NSX logical networks. The same logical networks are available across the vCenter NSX environment, so it's possible for VMs on any cluster on any vCenter Server system to be connected to the same logical network.
- Centralized security policy management. Firewall rules are managed from one centralized
location , and apply to the VM regardless of location or vCenter Server system. - Support of new mobility boundaries in vSphere 6, including cross vCenter and long distance vMotion across logical switches.
- Enhanced support for multi-site environments, from
metro distance to 150ms RTT. This includes both active-active and active-passive datacenters. - Centralized management of universal objects, reducing administration effort.
- Increased mobility of workloads - VMs can be vMotioned across vCenter Servers without having to reconfigure the VM or change firewall rules.
- Enhanced NSX multi-site and disaster recovery capabilities.
- Minimum numbers of NSX Universal Controllers required (e.g. my customer needed 4x3 UCC then onl 1x3UCC)
Linking (adding a Secondary NSX Manager) is pretty simple:
- Log in to the vCenter linked to the primary NSX Manager.
- Navigate to Home --> Networking & Security --> Installation and select the Management tab.
- Click the primary NSX Manager. Then select Actions --> Add Secondary NSX Manager.
- Enter the IP address, username, and password of the secondary NSX Manager. Click OK.
I needed to change 4x 1Primary +1Secondary topology to 1Primary + 7x Secondary. This is not a complex task until you do not have overlapping segment id. When you link Secondary to Primary NSX, you have to make sure that segment id that you specified on the Secondary is unique within all NSX domains in Cross-vCenter environment. If you face an issue with overlapping VNI (segment id) used by Logical Switches in each standalone NSX domain, you have to remove all Logical Switches and reconfigure range of default segment or try to change VNI of Logical Switches. To change cross-vCenter NSX topology (changing primary/secondary linking) you can perform the below steps:
- Change an old Primary NSX Manager to Transit (Secondary is changed to Transit as well). Click the primary NSX Manager. Then select Actions --> Remove Primary Role.
- Rewrite required universal firewall rules to a new Primary (script or manually). Then remove them from the old Primary (already Transit) - a really useful script to clean universal objects - available here.
- Change the NSX Manager from Transit to Standalone: Actions --> Set as Standalone.
- Link to a new primary.
Repeat 1-4 for each Primary that you want to re-link and 2-4 for each Secondary.
Cross-vCenter NSX is a nice feature but there are some limitations of this topology as the